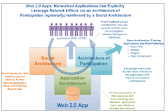
Tagging—individuals using keywords of their own choosing to classify objects online,
including photos, bookmarks, products, and blog posts—is common with Web 2.0-
style sites. These folksonomies (a neologism derived from “folks” and “taxonomy”) provide
a number of benefits:
Hierarchies by definition are top-down and typically defined in a centralized
fashion, which is an impractical model poorly suited to the collaborative,
decentralized, highly networked world of Web 2.0.
Rich media, such as audio and video, benefit from this explicit metadata because
other forms of extracting meaning and searching is still a challenge.
Tags facilitate second-order effects by virtue of the aggregate, collective
intelligence that can be mined from the data set (enough to overcome differences
in individual tag choices for identical items).
Issues & Debates
Walled gardens 2.0. In Web 1.0, America Online (AOL) exemplified the
walled garden: users were welcome to create content and community as long
as it occurred within the walls of AOL. Arguably, there are now Web 2.0
walled gardens, such as MySpace and LinkedIn, which have vibrant, but—in
many ways—closed communities.
Privacy and liability for individuals. People are revealing increasingly more
details about themselves online, including likes, dislikes, opinions, personal
history, relationships, purchasing history, work history, dating history, and
so on. Therefore, it is increasingly being mined by other people, including
employers performing background checks, singles investigating upcoming
dates, government agencies mining social networking sites,36 and tax assessors
using homeowners’ online comments about remodeling upgrades to increase
property taxes.37
Privacy and liability for providers. Not being sufficiently sensitive to privacy
issues can result in legal and public relations disasters. Facebook suffered
some high-profile PR fallout when it underestimated the privacy implications
of new features deployed in September 2006. Within days, it was
forced to retract statements it had made and change service behavior.38 Or,
consider the $1 million fine issued to Xanga by the U.S. Federal Trade Commission
for violating the Children’s Online Privacy Protection Act (COPPA).
Xanga allowed children who identified themselves as under 13 years old
to sign-up for accounts, even though the stated policy forbid providing
accounts to that age group.39
Quality, not just quantity, matters. All users are not created equal nor are
their contributions. The most successful Web 2.0 companies have instituted
mechanisms to encourage and reward their most valuable members.
Monday, December 17, 2007
WEB 2.0 The Eight Core Patterns
Harnessing Collective Intelligence
Create an architecture of participation that uses network effects and algorithms to
produce software that gets better the more people use it.
Data Is the Next “Intel Inside”
Use unique, hard-to-recreate data sources to become the “Intel Inside” for this era
in which data has become as important as function.
Innovation in Assembly
Build platforms to foster innovation in assembly, where remixing of data and services
creates new opportunities and markets.
Rich User Experiences
Go beyond traditional web-page metaphors to deliver rich user experiences combining
the best of desktop and online software.
Software Above the Level of a Single Device
Create software that spans Internet-connected devices and builds on the growing
pervasiveness of online experience.
Perpetual Beta
Move away from old models of software development and adoption in favor of
online, continuously updated, software as a service (SaaS) models.
The Eight Core
Patterns
11 Web 2.0 Principles and Best Practices
Leveraging the Long Tail
Capture niche markets profitably through the low-cost economics and broad reach
enabled by the Internet.
Lightweight Models and Cost-Effective Scalability
Use lightweight business- and software-development models to build products and
businesses quickly and cost-effectively.
Although each pattern is unique, they are by no means independent. In fact, they are
quite interdependent.
A set of common Web 2.0 attributes supports these patterns:
Massively connected. Network effects move us from the one-to-many
publishing and communication models of the past into a true web of manyto-
many connections. In this era, the edges become as important as the core,
and old modes of communication, publishing, distribution, and aggregation
become disrupted.
Decentralized. Connectedness also disrupts traditional control and power
structures, leading to much greater decentralization. Bottom-up now competes
with top-down in everything from global information flow to marketing
to new product design. Adoption occurs via pull not push. Systems often
grow from the edges in, not from the core out.
User focused. The user is at the center of Web 2.0. Network effects give
users unprecedented power for participation, conversation, collaboration,
and, ultimately, impact. Consumers have become publishers with greater
control, experiences are tailored on the fly for each user, rich interfaces optimize
user interactions, users actively shape product direction, and consumers
reward companies that treat them well with loyalty and valuable word-ofmouth
marketing.
Open. In Web 2.0, openness begins with the foundation of the Internet’s
open technology standards and rapidly grows into an open ecosystem of
loosely coupled applications built on open data, open APIs, and reusable
components. And open means more than technology—it means greater
transparency in corporate communications, shared intellectual property, and
greater visibility into how products are developed.
Lightweight. A “less is more, keep it simple” philosophy permeates Web 2.0:
software is designed and built by small teams using agile methods; technology
solutions build on simple data formats and protocols; software becomes
simple to deploy with light footprint services built on open source software;
business focuses on keeping investment and costs low; and marketing uses
simple consumer-to-consumer viral techniques.
Emergent. Rather than relying on fully predefined application structures,
Web 2.0 structures and behaviors are allowed to emerge over time. A flexible,
adaptive strategy permits appropriate solutions to evolve in response to realworld
usage; success comes from cooperation, not control.
Create an architecture of participation that uses network effects and algorithms to
produce software that gets better the more people use it.
Data Is the Next “Intel Inside”
Use unique, hard-to-recreate data sources to become the “Intel Inside” for this era
in which data has become as important as function.
Innovation in Assembly
Build platforms to foster innovation in assembly, where remixing of data and services
creates new opportunities and markets.
Rich User Experiences
Go beyond traditional web-page metaphors to deliver rich user experiences combining
the best of desktop and online software.
Software Above the Level of a Single Device
Create software that spans Internet-connected devices and builds on the growing
pervasiveness of online experience.
Perpetual Beta
Move away from old models of software development and adoption in favor of
online, continuously updated, software as a service (SaaS) models.
The Eight Core
Patterns
11 Web 2.0 Principles and Best Practices
Leveraging the Long Tail
Capture niche markets profitably through the low-cost economics and broad reach
enabled by the Internet.
Lightweight Models and Cost-Effective Scalability
Use lightweight business- and software-development models to build products and
businesses quickly and cost-effectively.
Although each pattern is unique, they are by no means independent. In fact, they are
quite interdependent.
A set of common Web 2.0 attributes supports these patterns:
Massively connected. Network effects move us from the one-to-many
publishing and communication models of the past into a true web of manyto-
many connections. In this era, the edges become as important as the core,
and old modes of communication, publishing, distribution, and aggregation
become disrupted.
Decentralized. Connectedness also disrupts traditional control and power
structures, leading to much greater decentralization. Bottom-up now competes
with top-down in everything from global information flow to marketing
to new product design. Adoption occurs via pull not push. Systems often
grow from the edges in, not from the core out.
User focused. The user is at the center of Web 2.0. Network effects give
users unprecedented power for participation, conversation, collaboration,
and, ultimately, impact. Consumers have become publishers with greater
control, experiences are tailored on the fly for each user, rich interfaces optimize
user interactions, users actively shape product direction, and consumers
reward companies that treat them well with loyalty and valuable word-ofmouth
marketing.
Open. In Web 2.0, openness begins with the foundation of the Internet’s
open technology standards and rapidly grows into an open ecosystem of
loosely coupled applications built on open data, open APIs, and reusable
components. And open means more than technology—it means greater
transparency in corporate communications, shared intellectual property, and
greater visibility into how products are developed.
Lightweight. A “less is more, keep it simple” philosophy permeates Web 2.0:
software is designed and built by small teams using agile methods; technology
solutions build on simple data formats and protocols; software becomes
simple to deploy with light footprint services built on open source software;
business focuses on keeping investment and costs low; and marketing uses
simple consumer-to-consumer viral techniques.
Emergent. Rather than relying on fully predefined application structures,
Web 2.0 structures and behaviors are allowed to emerge over time. A flexible,
adaptive strategy permits appropriate solutions to evolve in response to realworld
usage; success comes from cooperation, not control.
Ingredients of Web 2.0 Success
Web 2.0 is a set of social, economic, and technology trends that collectively
form the basis for the next generation of the Internet—a more mature,
distinct medium characterized by user participation, openness, and
network effects.
Web 2.0 did not materialize overnight. It represents the evolution and maturation of
the Internet during the past decade. The Internet, like other new mediums, began by
mimicking those that came before, but only time and experience revealed its unique
strengths. In many ways, Web 2.0 is a rediscovery or fulfillment of what the Web was
intended to be.26
The impact of Web 2.0 is now accelerating as the network grows and becomes more
ingrained into the daily lives of individuals and organizations. Yet Web 2.0 as a label
has become part of the vernacular because it concisely conveys just enough meaning—
in particular, that we are entering a distinct new era—to become the basis for
this worldwide dialog. The definition of Web 2.0 is a starting point because, in the
end, it is the underlying patterns that are much more important than a definition.
Understanding these patterns is the key to success in Web 2.0.
form the basis for the next generation of the Internet—a more mature,
distinct medium characterized by user participation, openness, and
network effects.
Web 2.0 did not materialize overnight. It represents the evolution and maturation of
the Internet during the past decade. The Internet, like other new mediums, began by
mimicking those that came before, but only time and experience revealed its unique
strengths. In many ways, Web 2.0 is a rediscovery or fulfillment of what the Web was
intended to be.26
The impact of Web 2.0 is now accelerating as the network grows and becomes more
ingrained into the daily lives of individuals and organizations. Yet Web 2.0 as a label
has become part of the vernacular because it concisely conveys just enough meaning—
in particular, that we are entering a distinct new era—to become the basis for
this worldwide dialog. The definition of Web 2.0 is a starting point because, in the
end, it is the underlying patterns that are much more important than a definition.
Understanding these patterns is the key to success in Web 2.0.
How Consumers Are Leading the Way to Enterprise 2.0
In earlier eras, computing innovation was originally driven by investments in the military
and enterprise sectors, and later moved into the consumer space. However, we are
now seeing consumers leading the way by virtue of their high-performance computers,
broadband connections, comfort with the medium, and ready access to powerful
online applications. This will reach IT from at least two distinct directions:
Consumers’ experience with Web 2.0-class software is setting the bar of what
software can and should be. Consumers are bringing that knowledge, as well as
those expectations, into their roles as corporate employees.
Enterprise software vendors are learning how to effectively incorporate Web 2.0
principles into their product and service offerings.
Web 2.0’s inevitable arrival within the enterprise is likely to follow the pattern set by
earlier disruptions, such as personal computers or instant messaging, and infiltrate
organizations in a decentralized, bottom-up fashion, only to become pervasive and
essential.
Impact: Web 2.0 is leading to Enterprise 2.0—CIOs and IT executives will only succeed
if they are ahead of the curve through an understanding of the workplace benefits and
challenges of Web 2.0. The differences in needs and culture “behind the firewall” mean
adapting external models to the appropriate internal ones. Enterprises can learn from
consumer Web 2.0 lessons, such as massive scaling, capturing network effects, and creating
rich user experiences.
Although each of these trends has impact and meaning unto itself, the truly significant
consequence comes from the fact that they are all occurring simultaneously. The
most successful Web 2.0 products and companies are capitalizing on:
New business models facilitated by changes in infrastructure costs, the reach
of the Long Tail, viral network-driven marketing, and new advertising-based
revenue opportunities.
New social models in which user-generated content can be as valuable as
traditional media, where social networks form and grow with tremendous
speed, where truly global audiences can be reached more easily, and rich
media from photos to videos is a part of everyday life online.
New technology models in which software becomes a service; the Internet
becomes the development platform, where online services and data are mixed
and matched; syndication of content becomes glue across the network; and
high-speed, ubiquitous access is the norm.
These models are bound together in an era where network effects rapidly drive viral
growth, where data rather than function is the core value of applications, and customers
now think of applications as services they use, not software they install.
and enterprise sectors, and later moved into the consumer space. However, we are
now seeing consumers leading the way by virtue of their high-performance computers,
broadband connections, comfort with the medium, and ready access to powerful
online applications. This will reach IT from at least two distinct directions:
Consumers’ experience with Web 2.0-class software is setting the bar of what
software can and should be. Consumers are bringing that knowledge, as well as
those expectations, into their roles as corporate employees.
Enterprise software vendors are learning how to effectively incorporate Web 2.0
principles into their product and service offerings.
Web 2.0’s inevitable arrival within the enterprise is likely to follow the pattern set by
earlier disruptions, such as personal computers or instant messaging, and infiltrate
organizations in a decentralized, bottom-up fashion, only to become pervasive and
essential.
Impact: Web 2.0 is leading to Enterprise 2.0—CIOs and IT executives will only succeed
if they are ahead of the curve through an understanding of the workplace benefits and
challenges of Web 2.0. The differences in needs and culture “behind the firewall” mean
adapting external models to the appropriate internal ones. Enterprises can learn from
consumer Web 2.0 lessons, such as massive scaling, capturing network effects, and creating
rich user experiences.
Although each of these trends has impact and meaning unto itself, the truly significant
consequence comes from the fact that they are all occurring simultaneously. The
most successful Web 2.0 products and companies are capitalizing on:
New business models facilitated by changes in infrastructure costs, the reach
of the Long Tail, viral network-driven marketing, and new advertising-based
revenue opportunities.
New social models in which user-generated content can be as valuable as
traditional media, where social networks form and grow with tremendous
speed, where truly global audiences can be reached more easily, and rich
media from photos to videos is a part of everyday life online.
New technology models in which software becomes a service; the Internet
becomes the development platform, where online services and data are mixed
and matched; syndication of content becomes glue across the network; and
high-speed, ubiquitous access is the norm.
These models are bound together in an era where network effects rapidly drive viral
growth, where data rather than function is the core value of applications, and customers
now think of applications as services they use, not software they install.
Executive Summary WEB 2. 0
Web 2.0 is a set of economic, social, and technology trends that collectively
form the basis for the next generation of the Internet—a more mature,
distinctive medium characterized by user participation, openness, and
network effects.
Web 2.0 is here today, yet its vast disruptive impact is just beginning. More than just
the latest technology buzzword, it’s a transformative force that’s propelling companies
across all industries toward a new way of doing business. Those who act on the Web
2.0 opportunity stand to gain an early-mover advantage in their markets.
O’Reilly Media has identified eight core patterns that are keys to understanding and
navigating the Web 2.0 era. This report details the problems each pattern solves or
opportunities it creates, and provides a thorough analysis of market trends, proven
best practices, case studies of industry leaders, and tools for hands-on self-assessment.
To compete and thrive in today’s Web 2.0 world, technology decision-makers—
including
executives, product strategists, entrepreneurs, and thought leaders—need
to act now, before the market settles into a new equilibrium. This report shows you
how.
What’s causing this change? Consider the following raw demographic and technological
drivers:
One billion people around the globe now have access to the Internet
Mobile devices outnumber desktop computers by a factor of two
Nearly 50 percent of all U.S. Internet access is now via always-on broadband
connections
Combine drivers with the fundamental laws of social networks and lessons from the
Web’s first decade, and:
In the first quarter of 2006, MySpace.com signed up 280,000 new users each
day and had the second most Internet traffic
By the second quarter of 2006, 50 million blogs were created—new ones
were added at a rate of two per second
In 2005, eBay conducted 8 billion API-based web services transactions
These trends manifest themselves under a variety of guises, names, and technologies:
social computing, user-generated content, software as a service, podcasting, blogs,
and the read–write web. Taken together, they are Web 2.0, the next-generation, userdriven,
intelligent web. This report is a guide to understanding the principles of Web
2.0 today, providing you with the information and tools you need to implement Web
2.0 concepts in your own products and organization.
form the basis for the next generation of the Internet—a more mature,
distinctive medium characterized by user participation, openness, and
network effects.
Web 2.0 is here today, yet its vast disruptive impact is just beginning. More than just
the latest technology buzzword, it’s a transformative force that’s propelling companies
across all industries toward a new way of doing business. Those who act on the Web
2.0 opportunity stand to gain an early-mover advantage in their markets.
O’Reilly Media has identified eight core patterns that are keys to understanding and
navigating the Web 2.0 era. This report details the problems each pattern solves or
opportunities it creates, and provides a thorough analysis of market trends, proven
best practices, case studies of industry leaders, and tools for hands-on self-assessment.
To compete and thrive in today’s Web 2.0 world, technology decision-makers—
including
executives, product strategists, entrepreneurs, and thought leaders—need
to act now, before the market settles into a new equilibrium. This report shows you
how.
What’s causing this change? Consider the following raw demographic and technological
drivers:
One billion people around the globe now have access to the Internet
Mobile devices outnumber desktop computers by a factor of two
Nearly 50 percent of all U.S. Internet access is now via always-on broadband
connections
Combine drivers with the fundamental laws of social networks and lessons from the
Web’s first decade, and:
In the first quarter of 2006, MySpace.com signed up 280,000 new users each
day and had the second most Internet traffic
By the second quarter of 2006, 50 million blogs were created—new ones
were added at a rate of two per second
In 2005, eBay conducted 8 billion API-based web services transactions
These trends manifest themselves under a variety of guises, names, and technologies:
social computing, user-generated content, software as a service, podcasting, blogs,
and the read–write web. Taken together, they are Web 2.0, the next-generation, userdriven,
intelligent web. This report is a guide to understanding the principles of Web
2.0 today, providing you with the information and tools you need to implement Web
2.0 concepts in your own products and organization.
Web 2.0 Design Patterns
In his book, A Pattern Language, Christopher Alexander prescribes a format for the concise description of the solution to architectural problems. He writes: "Each pattern describes a problem that occurs over and over again in our environment, and then describes the core of the solution to that problem, in such a way that you can use this solution a million times over, without ever doing it the same way twice."
The Long Tail
Small sites make up the bulk of the internet's content; narrow niches make up the bulk of internet's the possible applications. Therefore: Leverage customer-self service and algorithmic data management to reach out to the entire web, to the edges and not just the center, to the long tail and not just the head.
Data is the Next Intel Inside
Applications are increasingly data-driven. Therefore: For competitive advantage, seek to own a unique, hard-to-recreate source of data.
Users Add Value
The key to competitive advantage in internet applications is the extent to which users add their own data to that which you provide. Therefore: Don't restrict your "architecture of participation" to software development. Involve your users both implicitly and explicitly in adding value to your application.
Network Effects by Default
Only a small percentage of users will go to the trouble of adding value to your application. Therefore: Set inclusive defaults for aggregating user data as a side-effect of their use of the application.
Some Rights Reserved. Intellectual property protection limits re-use and prevents experimentation. Therefore: When benefits come from collective adoption, not private restriction, make sure that barriers to adoption are low. Follow existing standards, and use licenses with as few restrictions as possible. Design for "hackability" and "remixability."
The Perpetual Beta
When devices and programs are connected to the internet, applications are no longer software artifacts, they are ongoing services. Therefore: Don't package up new features into monolithic releases, but instead add them on a regular basis as part of the normal user experience. Engage your users as real-time testers, and instrument the service so that you know how people use the new features.
Cooperate, Don't Control
Web 2.0 applications are built of a network of cooperating data services. Therefore: Offer web services interfaces and content syndication, and re-use the data services of others. Support lightweight programming models that allow for loosely-coupled systems.
Software Above the Level of a Single Device
The PC is no longer the only access device for internet applications, and applications that are limited to a single device are less valuable than those that are connected. Therefore: Design your application from the get-go to integrate services across handheld devices, PCs, and internet servers.
The Long Tail
Small sites make up the bulk of the internet's content; narrow niches make up the bulk of internet's the possible applications. Therefore: Leverage customer-self service and algorithmic data management to reach out to the entire web, to the edges and not just the center, to the long tail and not just the head.
Data is the Next Intel Inside
Applications are increasingly data-driven. Therefore: For competitive advantage, seek to own a unique, hard-to-recreate source of data.
Users Add Value
The key to competitive advantage in internet applications is the extent to which users add their own data to that which you provide. Therefore: Don't restrict your "architecture of participation" to software development. Involve your users both implicitly and explicitly in adding value to your application.
Network Effects by Default
Only a small percentage of users will go to the trouble of adding value to your application. Therefore: Set inclusive defaults for aggregating user data as a side-effect of their use of the application.
Some Rights Reserved. Intellectual property protection limits re-use and prevents experimentation. Therefore: When benefits come from collective adoption, not private restriction, make sure that barriers to adoption are low. Follow existing standards, and use licenses with as few restrictions as possible. Design for "hackability" and "remixability."
The Perpetual Beta
When devices and programs are connected to the internet, applications are no longer software artifacts, they are ongoing services. Therefore: Don't package up new features into monolithic releases, but instead add them on a regular basis as part of the normal user experience. Engage your users as real-time testers, and instrument the service so that you know how people use the new features.
Cooperate, Don't Control
Web 2.0 applications are built of a network of cooperating data services. Therefore: Offer web services interfaces and content syndication, and re-use the data services of others. Support lightweight programming models that allow for loosely-coupled systems.
Software Above the Level of a Single Device
The PC is no longer the only access device for internet applications, and applications that are limited to a single device are less valuable than those that are connected. Therefore: Design your application from the get-go to integrate services across handheld devices, PCs, and internet servers.
Web 2.0 Design Patterns
In his book, A Pattern Language, Christopher Alexander prescribes a format for the concise description of the solution to architectural problems. He writes: "Each pattern describes a problem that occurs over and over again in our environment, and then describes the core of the solution to that problem, in such a way that you can use this solution a million times over, without ever doing it the same way twice."
The Long Tail
Small sites make up the bulk of the internet's content; narrow niches make up the bulk of internet's the possible applications. Therefore: Leverage customer-self service and algorithmic data management to reach out to the entire web, to the edges and not just the center, to the long tail and not just the head.
Data is the Next Intel Inside
Applications are increasingly data-driven. Therefore: For competitive advantage, seek to own a unique, hard-to-recreate source of data.
Users Add Value
The key to competitive advantage in internet applications is the extent to which users add their own data to that which you provide. Therefore: Don't restrict your "architecture of participation" to software development. Involve your users both implicitly and explicitly in adding value to your application.
Network Effects by Default
Only a small percentage of users will go to the trouble of adding value to your application. Therefore: Set inclusive defaults for aggregating user data as a side-effect of their use of the application.
Some Rights Reserved. Intellectual property protection limits re-use and prevents experimentation. Therefore: When benefits come from collective adoption, not private restriction, make sure that barriers to adoption are low. Follow existing standards, and use licenses with as few restrictions as possible. Design for "hackability" and "remixability."
The Perpetual Beta
When devices and programs are connected to the internet, applications are no longer software artifacts, they are ongoing services. Therefore: Don't package up new features into monolithic releases, but instead add them on a regular basis as part of the normal user experience. Engage your users as real-time testers, and instrument the service so that you know how people use the new features.
Cooperate, Don't Control
Web 2.0 applications are built of a network of cooperating data services. Therefore: Offer web services interfaces and content syndication, and re-use the data services of others. Support lightweight programming models that allow for loosely-coupled systems.
Software Above the Level of a Single Device
The PC is no longer the only access device for internet applications, and applications that are limited to a single device are less valuable than those that are connected. Therefore: Design your application from the get-go to integrate services across handheld devices, PCs, and internet servers.
The Long Tail
Small sites make up the bulk of the internet's content; narrow niches make up the bulk of internet's the possible applications. Therefore: Leverage customer-self service and algorithmic data management to reach out to the entire web, to the edges and not just the center, to the long tail and not just the head.
Data is the Next Intel Inside
Applications are increasingly data-driven. Therefore: For competitive advantage, seek to own a unique, hard-to-recreate source of data.
Users Add Value
The key to competitive advantage in internet applications is the extent to which users add their own data to that which you provide. Therefore: Don't restrict your "architecture of participation" to software development. Involve your users both implicitly and explicitly in adding value to your application.
Network Effects by Default
Only a small percentage of users will go to the trouble of adding value to your application. Therefore: Set inclusive defaults for aggregating user data as a side-effect of their use of the application.
Some Rights Reserved. Intellectual property protection limits re-use and prevents experimentation. Therefore: When benefits come from collective adoption, not private restriction, make sure that barriers to adoption are low. Follow existing standards, and use licenses with as few restrictions as possible. Design for "hackability" and "remixability."
The Perpetual Beta
When devices and programs are connected to the internet, applications are no longer software artifacts, they are ongoing services. Therefore: Don't package up new features into monolithic releases, but instead add them on a regular basis as part of the normal user experience. Engage your users as real-time testers, and instrument the service so that you know how people use the new features.
Cooperate, Don't Control
Web 2.0 applications are built of a network of cooperating data services. Therefore: Offer web services interfaces and content syndication, and re-use the data services of others. Support lightweight programming models that allow for loosely-coupled systems.
Software Above the Level of a Single Device
The PC is no longer the only access device for internet applications, and applications that are limited to a single device are less valuable than those that are connected. Therefore: Design your application from the get-go to integrate services across handheld devices, PCs, and internet servers.
Subscribe to:
Posts (Atom)